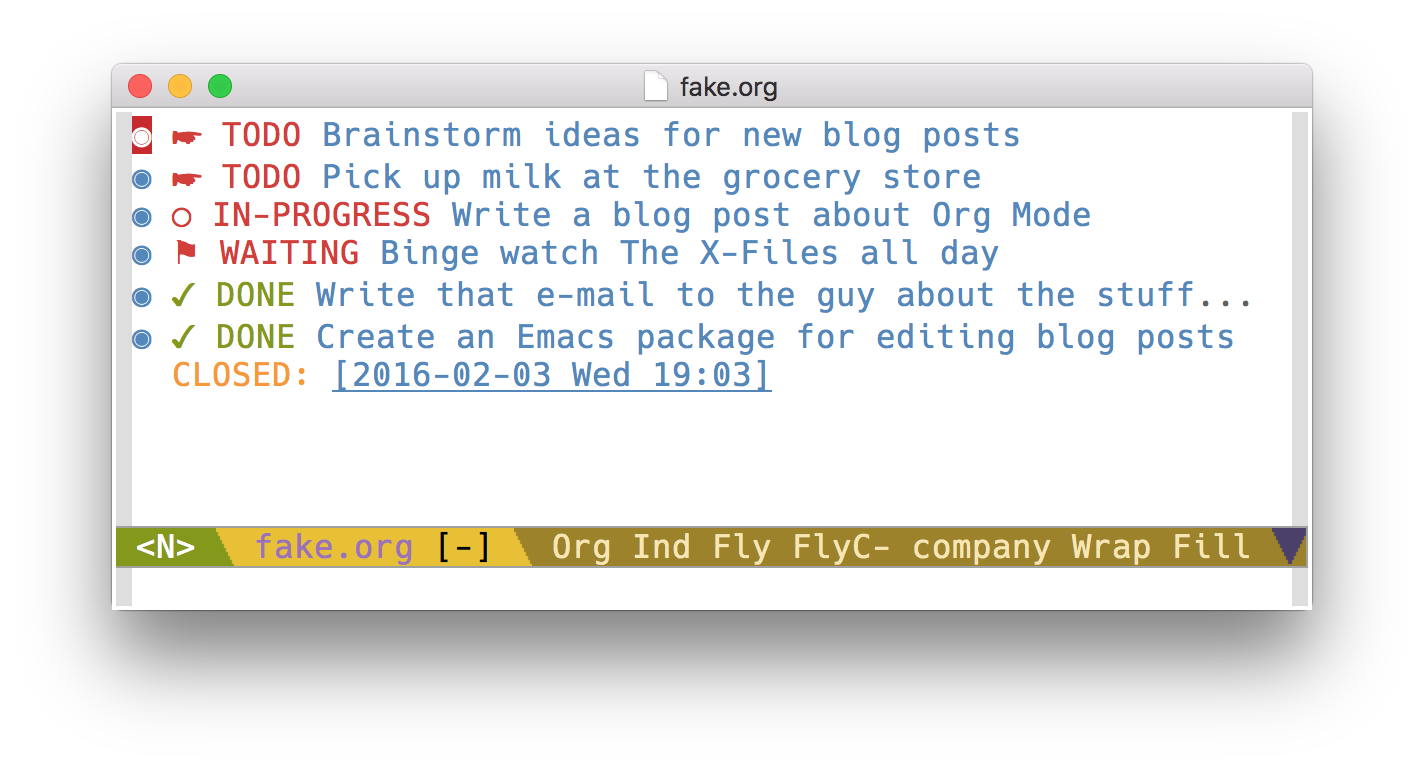
Org mode was one of the main reasons I tried Emacs (and left behind 15 years of Vim), and now it is a central part of how I organize my work. Org mode can help you take notes, track tasks, build agendas, process tabular data, and more. It’s so flexible that everyone uses it differently.
I use Org mode primarily to capture tasks and keep track of their progress. I sometimes take notes in Org mode, but I haven’t completely fleshed out my note-taking and searching workflow, so I’ll talk mostly about task management here.
